Quickly detect & remediate attacks on your web applications & APIs
$15.00/Year
Datadog Application Security Management allows you to manage application security risk with continuous, real-time monitoring of vulnerabilities and threats against your web applications, serverless applications, and APIs in production. Automatically integrated with APM distributed traces and code-level context, Application Security Management empowers development, operations, and security teams to build and run secure applications in production.
Top Features
Detect and defend against attacks
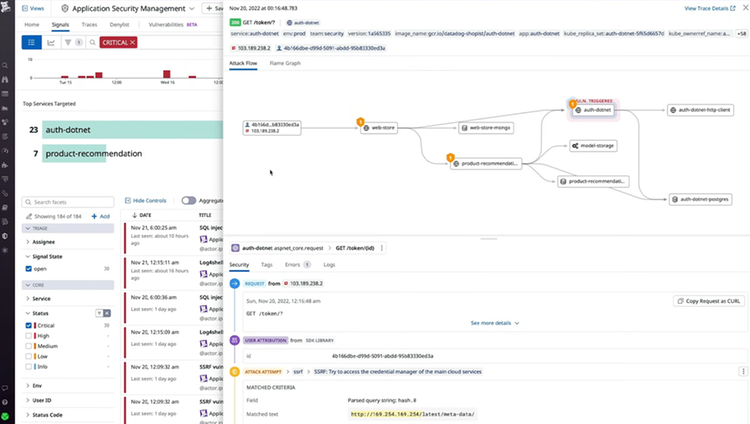
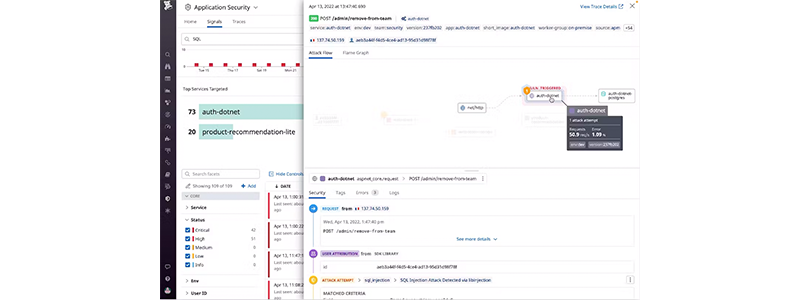
- Understand how ongoing threats targeting your web and serverless applications are propagating through your service chain with end-to-end attack flows.
- Pivot to errors, associated stack traces, and logs to easily collaborate across teams and eliminate bottlenecks.
- Slow down attackers by blocking suspicious requests or bad actors directly through the Datadog platform.
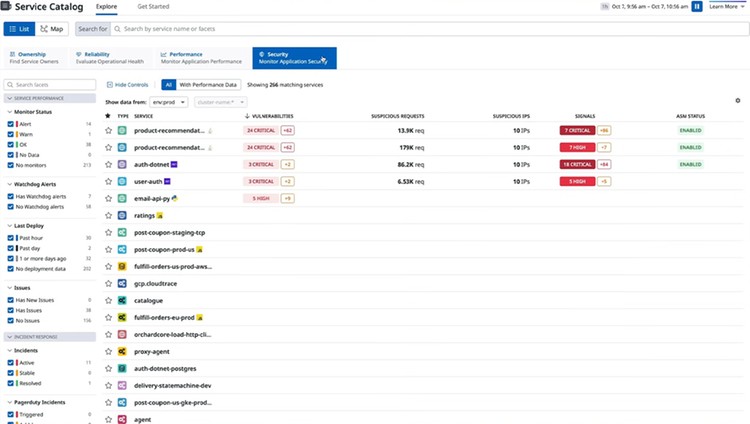
Automatically discover your API attack surface
- Gain visibility into the performance, security, and ownership of all your API endpoints in a single view.
- Surface the most targeted and at-risk endpoints to prioritize remediation efforts.
- Protect API endpoints by automatically blocking specific IPs, users, or requests.
Continuously monitor for code-level vulnerabilities in production
- Continuously identify vulnerabilities in application code serving production-level traffic, without the overhead of code scans or time-consuming testing processes.
- Identify the specific input or request that triggered the vulnerability in order to accelerate triage.
- Immediately see the exact vulnerable file, version, and line of code to reduce mean time to remediation.
Focus on open source vulnerabilities which present active risk
- Get end-to-end visibility into vulnerable open source libraries loaded across the CI and production.
- Prioritize open-source library vulnerabilities in your code and at runtime with Datadog’s Severity Score, which factors in exposure, CVSS, and real-time threat activity.
- Ensure remediated vulnerabilities make it to production and avoid discrepancies between static and runtime code due to errors in the CI/CD pipeline.
Recommended products
Improve Threat Detection with Context Awareness
- Quickly prioritize the remediation of the most business-critical threats with runtime execution context information.
- Detect OWASP attacks out of the box, including server-side-request forgeries (SSRFs), SQL injections, cross-site scripting (XSS) attacks, and more.
- Improve collaboration among development, security and operations teams with shared, code-level insights and alerts for faster remediation.
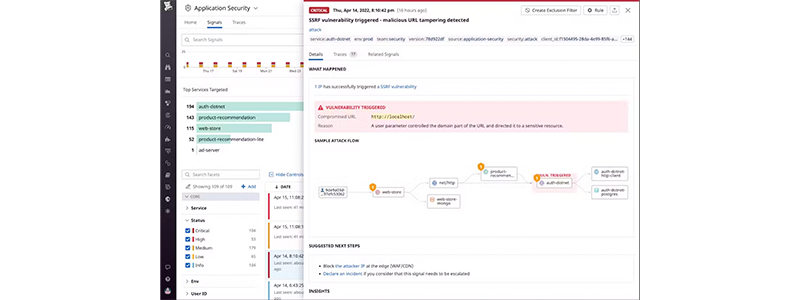
Identify Bad Actors
- Prioritize the most advanced attacks by flagging authenticated suspicious requests that target your authenticated attack surface.
- Easily identify the authenticated bad actors that are generating suspicious security activity and trace their activity.
- Quickly call attention to source IPs known to be suspicious by leveraging threat intelligence data.
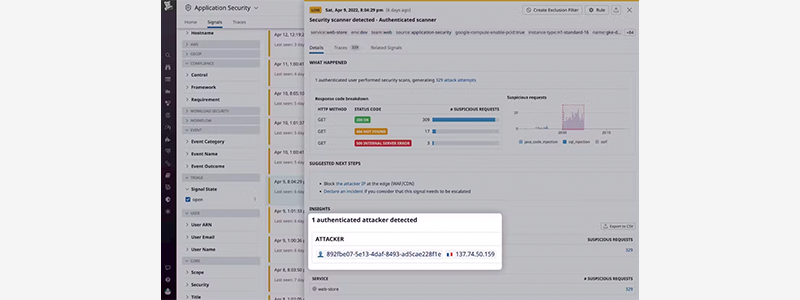
Gain Actionable Insights into Security Attacks
- Alert teams of attacks that have triggered code-level vulnerabilities.
- Gain deep visibility into how attacks affect applications and APIs by tracking their end-to-end attack flows.
- Align DevOps and Security together with full observability data and an easy-to-use, intuitive, unified platform.
Get Set Up in Minutes with 900+ Detection Rules and 700+ Integrations
- Improve your security and compliance posture with 900+ default detection rules mapped to the MITRE ATT&CK® and compliance frameworks.
- Discover in-depth insights into where issues are originating with 700+ vendor-backed integrations, including 100+ fully-supported AWS services.
- Create custom threat rules without learning a proprietary query language.
- Get full visibility into your network, identity providers, and SaaS applications with minimal configuration.

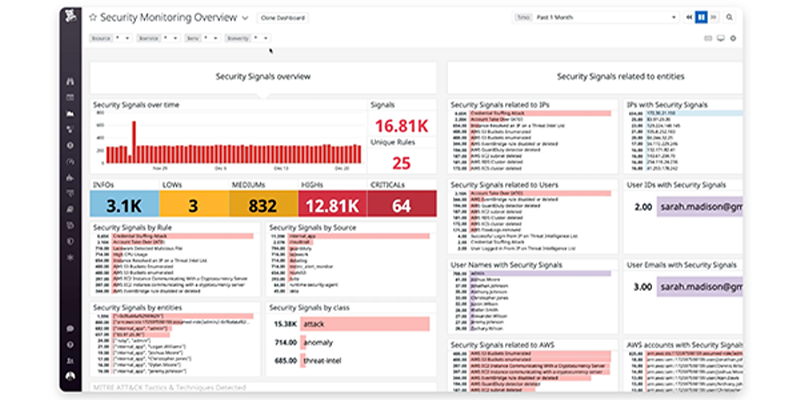
Respond to Threats Faster with A Low Maintenance, Cost-Effective SIEM
- Reduce your operational overhead with a cloud-native SIEM; focus on threat detection, not hardware maintenance.
- Rapidly analyze threats and easily filter security signals based on key attributes such as severity level, the MITRE ATT&CK® technique, or any associated entity, such as an attacker’s IP.
- Collaborate with multiple teams through integrations with ticketing portals, chat systems, and remediation tools.
Additional Information
Terms & Conditions
Terms of Service
https://www.datadoghq.com/legal/terms/Privacy Policy
https://www.datadoghq.com/legal/privacy/Resources
Data Application Security Management - Why T-Connecta Chose Datadog Application Security Management to Reduce Risk
Hear from the Infrastructure Manager at T-Connecta on how Datadog Application Security Management helps him to quickly reduce risk in his environment to prepare for annual penetration tests.