Complete cloud email security, deployed in minutes
$61,110.00/year
Proofpoint Security Tessian stops sophisticated email threats like BEC, ATO, and impersonation attacks that leverage modern tactics and procedures which bypass traditional email security controls. We use behavioral analysis and artificial intelligence to detect and prevent email based attacks. Built to enhance Microsoft and Google email environments, Tessian is deployed in minutes through native API integrations with email providers.
Top Features
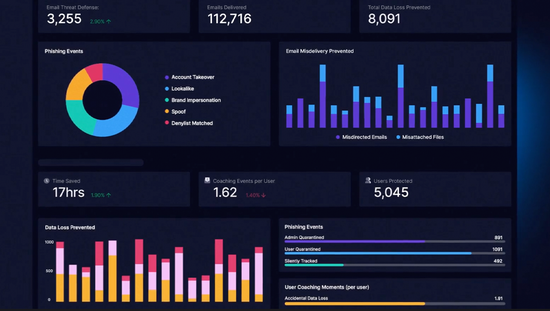
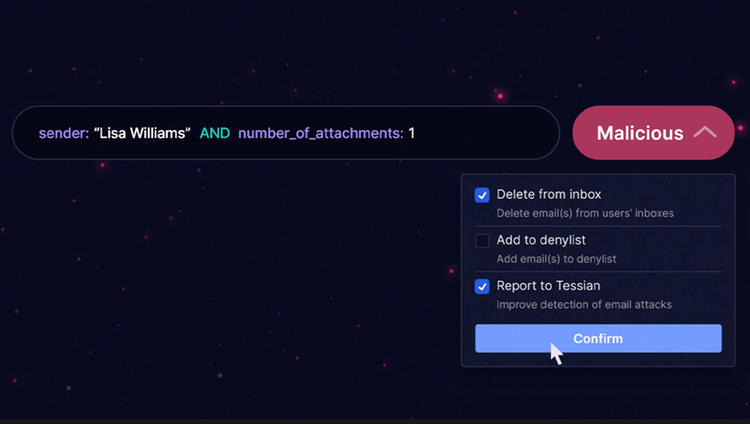
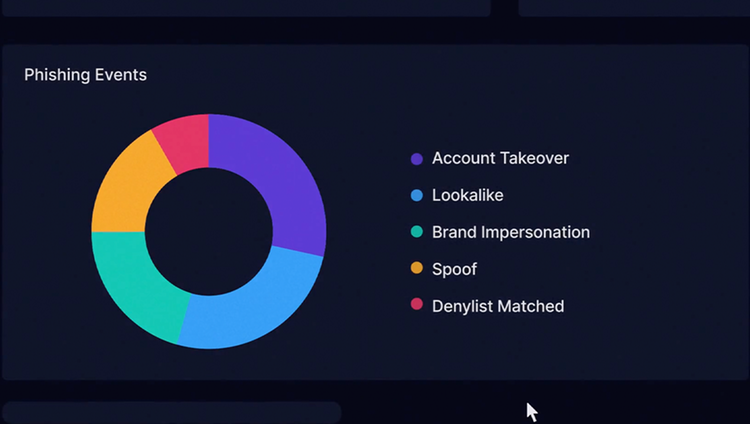
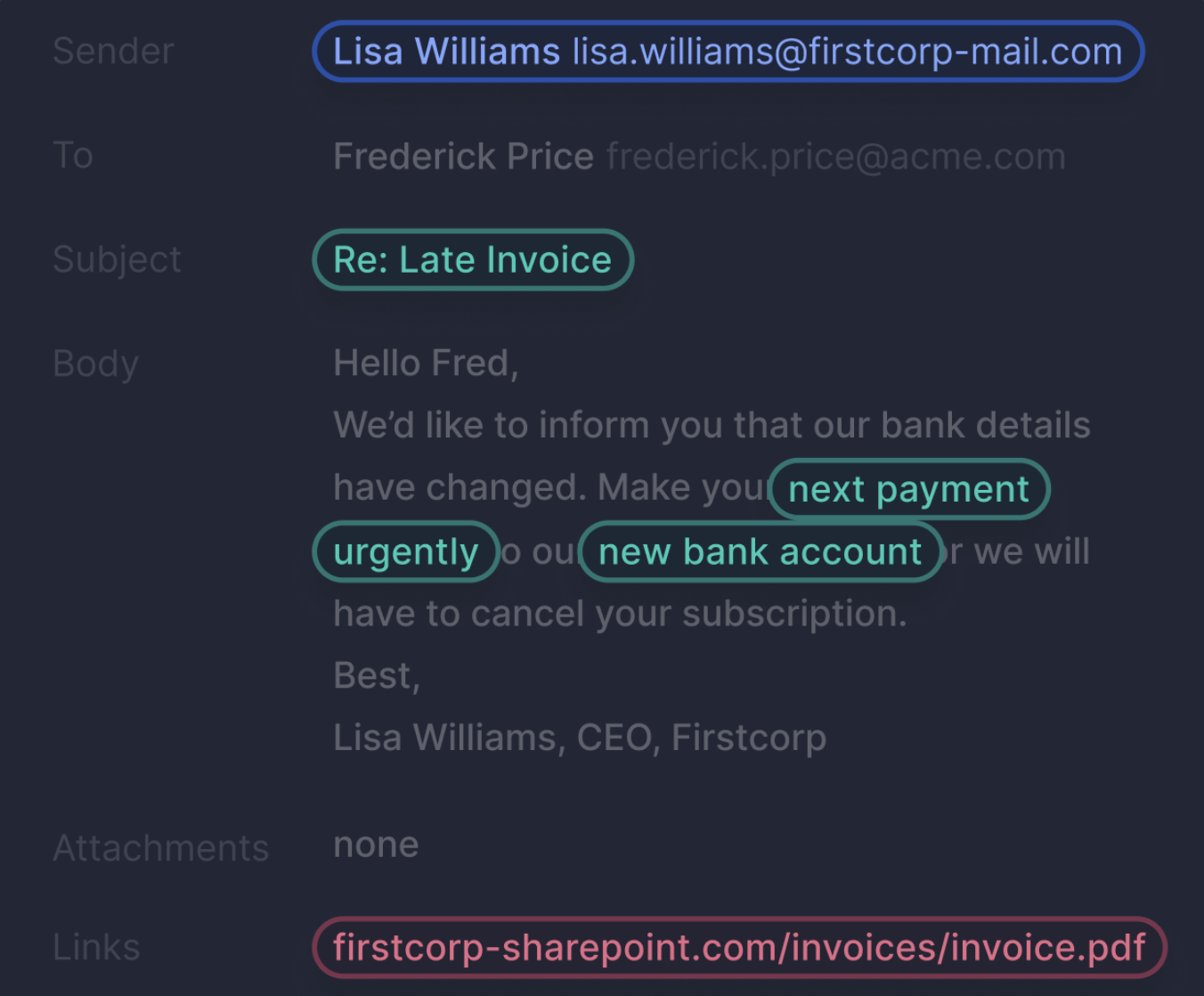
Defend against inbound email attacks
Stop advanced email threats like BEC, domain spoofing, impersonations, image based attacks including QR codes and more.
Protect sensitive data loss on email
Behavioral analysis to prevent employees from accidentally sending emails to the wrong people or exfiltrating sensitive data over email.
Respond to email incidents faster
Hunt, investigate, and respond to email threats with the industry’s fastest search and remediation. Automate removal of end user reported threats.
Coach end users in-the-moment
Empower users to make better security decisions with contextual warnings that teach them to assess risk and recognize potential threats.
Recommended products
Tessian AI Explained
Tessian uses an ensemble of AI based approaches because it's the only way to defend against advanced phishing attacks, and protect against sensitive data loss on email. Through behavioral, content and threat network analysis, Tessian AI automatically adjusts as our customers hire, acquire, and adapt.
Behavioral Analysis
Tessian AI uses millions signals to identify normal behavior vs. anomalous activity. Tens of thousands of historical events are used to build a strong behavioral baseline for each user.
Content Analysis
Tessian’s machine learning identifies threats in image-based text, QR codes, URLs, subject headings, body text, and inside of email attachments. Hundreds of data points within each email are used to determine if the email is safe, malicious, or needs review.
Threat Network Analysis
The Tessian platform uses a global threat library to improve security across the network. Within minutes, Tessian adds malicious domains, urls, IPs, email addresses and file hashes to prevent email based attacks across the entire Tessian community.
Additional Information
Terms & Conditions
Terms of Service
https://www.proofpoint.com/us/legal/licensePrivacy Policy
https://www.proofpoint.com/us/legal/privacy-policyResources
Proofpoint Security Tessian - Demo: Defend
Watch this video to learn more.
Proofpoint Security Tessian - Demo: Protect
Watch this video to learn more
Proofpoint Security Tessian - Demo: Respond
Watch this video to learn more.